About This Course
Learn How to Use MicroController in Real World Hacking Scenario
Learn How to Use MicroController in Real World Hacking Scenario
If you remember the scene from Mission Impossible 4 at Burj Khalifa in which Benji ask agent Ethan Hunt that they can not hack burj khalifa server room from inside. The only way to reach the server room is by climbing over the walls of the Burj and placing some hardware that contains malware and inserting it into the server. We going to see how we can create that hardware.
In this Course I’m going to show you how we can use tiny 1$ microcontroller to hack any PC on your local network as well as anywhere in the world using public IP.
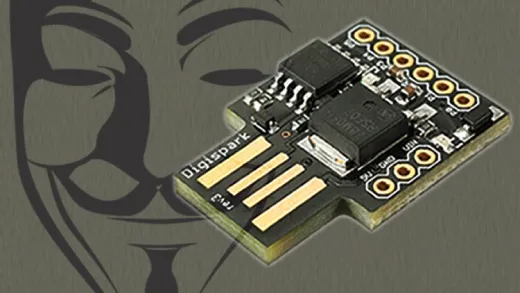
This Microcontroller is called DigiSpark. It is a microcontroller based on Attiny85 development board. It is similar to Arduino but smaller and more powerful in terms of hacking.








Juthawong N.
Short and straight forward